John: “Good morning, Sarah. I’ve been hearing a lot about the importance of access control devices and software lately. Can you shed some light on this topic for me?”
Sarah: Good morning, John. Certainly! Access control devices and software are crucial tools for security. They help us regulate who can enter specific areas and monitor those entries. Imagine them as the digital gatekeepers of our organization.
The importance of security cannot be overstated. Access control devices and software have emerged as critical solutions to secure people, assets, and sensitive information in today’s fast-paced environment, where security problems are always growing.
Businesses must invest in access control systems to protect sensitive data, secure physical buildings, or manage who has access to specified areas. These systems use a combination of hardware and software to control access, monitor activity, and improve overall security. In this blog post, we will explore the world of access control devices and software, their importance, and how they can benefit businesses and individuals alike.
Understanding Access Control Devices
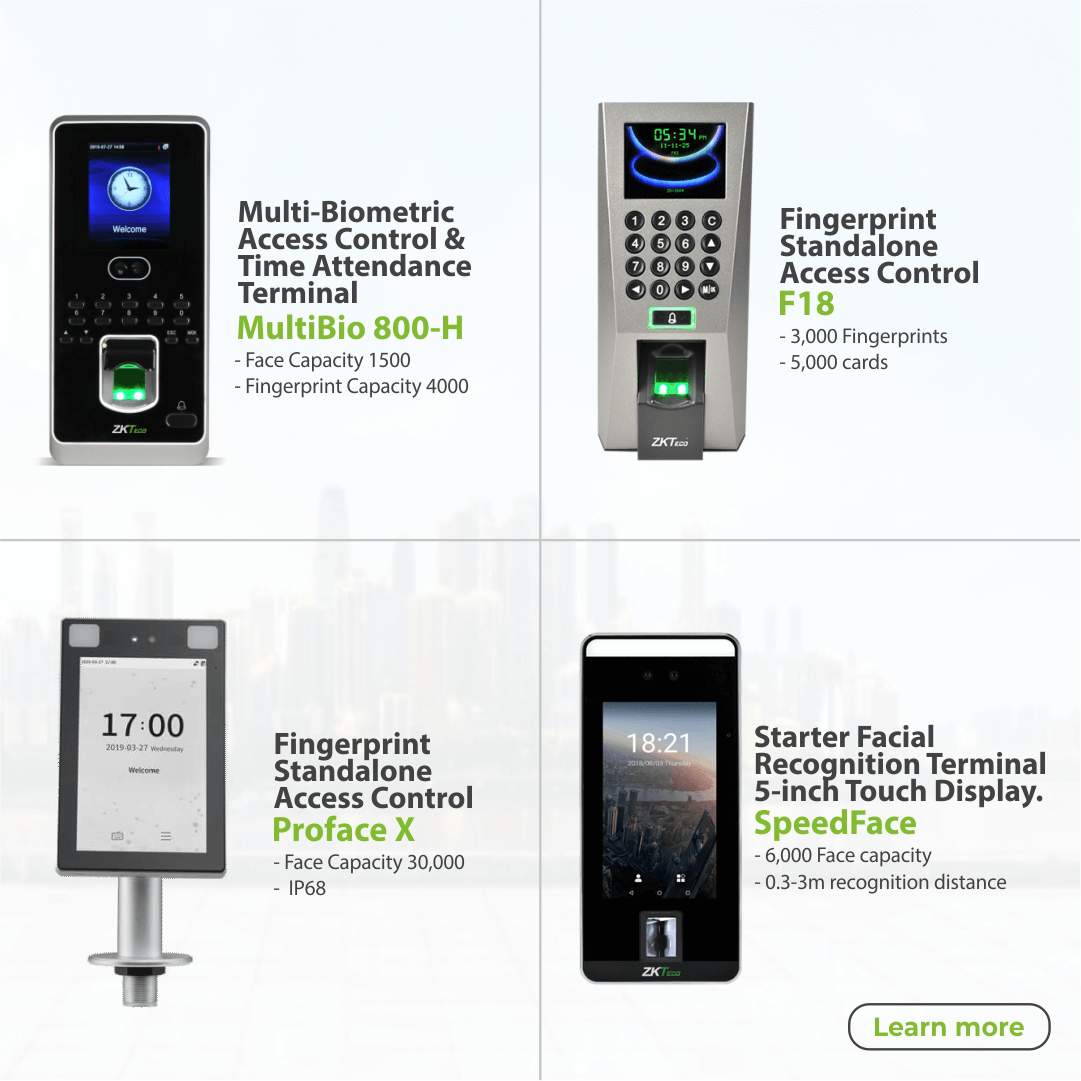
- Biometric Readers: Utilizing unique biological traits like fingerprints or facial recognition, biometric readers offer a high level of security by ensuring only authorized individuals gain access.
- Proximity Card Readers: Proximity card readers detect cards or fobs without direct contact, offering convenience and durability.
- Keypad and PIN Systems: Keypads and PIN systems require users to enter a code for entry, adding an additional layer of security.
- Exit Button: Exit button detects the wave of a hand through infrared without direct contact.

The Power of Access Control Software
While access control devices control physical entry, access control software serves as the digital brain behind the operation. Here’s why it’s equally crucial:
User Management: Access control software allows administrators to define who has access to specific areas, their access schedules, and the level of permissions they possess, ensuring a fine-grained approach to security.
Audit Trails: These comprehensive logs record every access event, providing a detailed history of who accessed where and when. They are invaluable for security monitoring and investigations.
Integration: Modern access control software often integrates seamlessly with other security systems such as video surveillance, alarms, and visitor management, creating a holistic security ecosystem.
Remote Access: Administrators can manage and monitor access remotely, granting flexibility and convenience, especially for large or distributed organizations.
Scalability: As businesses grow, access control software can easily scale to accommodate new users, areas, or security requirements.
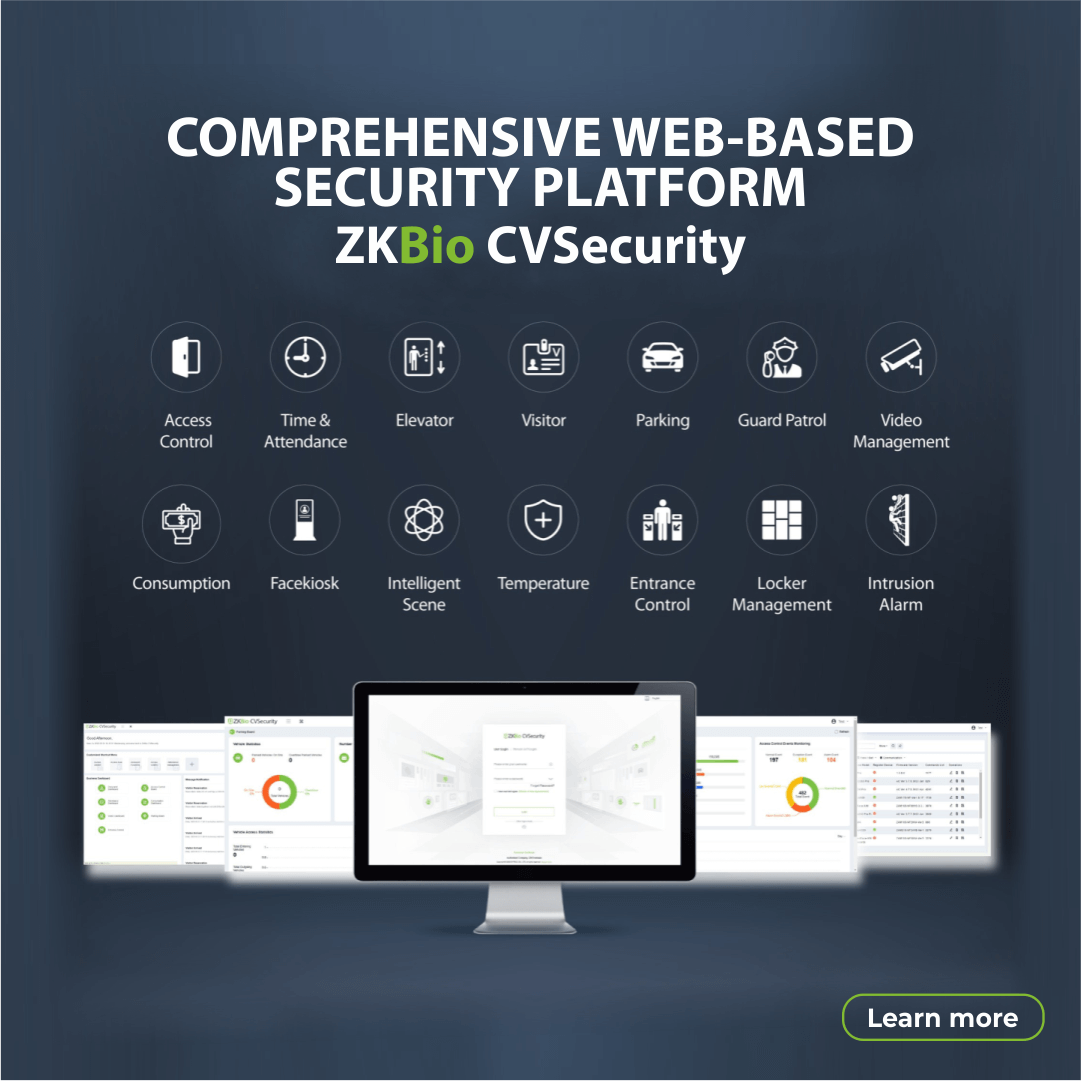
Benefits of Access Control Systems
Implementing access control devices and software offers a myriad of advantages:
Enhanced Security: Access control systems significantly boost security by preventing unauthorized access and providing robust monitoring capabilities.
Convenience: Users can access secured areas using various methods, making the process easy and efficient.
Cost Savings: Over time, access control systems reduce costs related to traditional locks and keys, such as rekeying and lock replacements.
Compliance: Access control systems aid in meeting regulatory requirements by providing comprehensive access logs and audit trails.
Efficiency: Access control software streamlines access rights management, making it easier for administrators to control access across the organization.
In Conclusion, access control devices and software have become pivotal in safeguarding assets, information, and people in today’s dynamic security landscape. Just as John and Sarah recognized their importance, organizations of all sizes should consider implementing these systems to protect their interests effectively. In a world where security threats continue to evolve, access control serves as a beacon of safety and control, ensuring that only the right people gain access to the right places at the right time.


